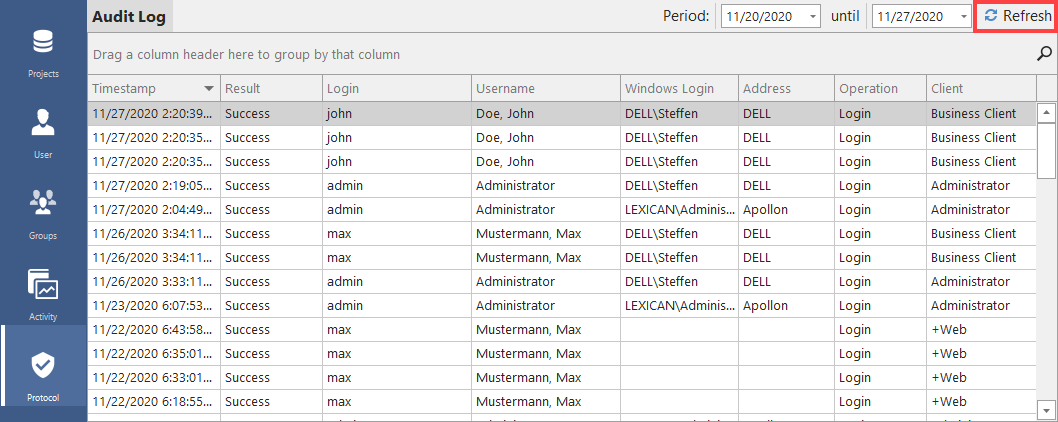
The security log provides information about which system logon was performed at a specific time. It shows the time, success/failure, ID, name and network ID of each user, and the name of the computer. The last column indicates whether the access was made through the client software or the web client +WEB.
The protocol continues indefinitely. If required, you can define a period of time to be examined in the upper right corner.
There you can also update the displayed data.